For the past two weeks I have been doing web application assessments. During this process I have had to try different tools to get the job done. During the trial and error process I can across some really cool tools, they are probably not new but new to me. The first is Charles proxy. This proxy is great for doing binary web application assessments allowing you to easily view the binary data being passed. A screen shot of Charles in action is below in Figure 1.
You can get the Charles proxy here.
Since I was looking at flash applications I needed analyze the swf file. While searching for a decent decomplier I found FileInsight by Secure Computing. Get FileInsight here:
This tools is great. It is a hex editor with collaborative reverse engineering in mind. Besides being a hex editor it allows you to do a number of actions I found to be useful:
-Breaks out PE header.
-Understands OLE2 structures.
-Ability to decode using multiple.
-Bookmark capability.
-Plug-ins for strings and an anomaly chart.
This will be replacing my other free and paid for hex editors, it is great cause it is free. It also looks to have a scripting capability that looks like it will come in handy.
On another note I spoke at the Defense Cyber Crime Conference last week. I addressed forensic issues on the Advanced Persistent Threat (APT). The talk is titled "Complex APT Forensics: Answering the Difficult Questions". You can get the sides and the customs Template and EnScripts from the following link:
APT M-unition Pack
Friday, January 23, 2009
Saturday, January 3, 2009
Extract OLE Objects with OLExtract
Recently I was challenged to see if I could extract files from Microsoft Office documents without a file header or footer. The files being put into the Microsoft documents were text files, configuration files and source code files. I do not know why these files were being put into office documents except maybe to hide the files. The files were not obfuscated in the documents and could be extracted manually. Extracting these files manually works for a small set of these documents but for a large set, manual extraction was not feasible. The location of these documents were on EnCase images so it made extracting them easier for me with an EnScript. The files in the office documents were kept as OLE objects. To view OLE objects in an office document within EnCase you can right click on the document and select "View File Structure". This action is shown in Figure 1 below.
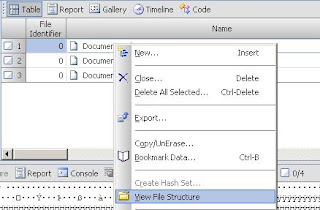
Figure 1 - Viewing Office Document "File Structure".
This also becomes a manual process viewing each document and then seeing what OLE objects are located in the document. EnCase recently came out with a way to automate the "View File Structure" process. The automated process is done with the File Mounter EnScript. This EnScript allows you to view the embedded file structure of many files such as Thumbs.db, zip archives, and Office documents (YES). Executing the process to automatically mount these types of files looks like Figure 2 below.
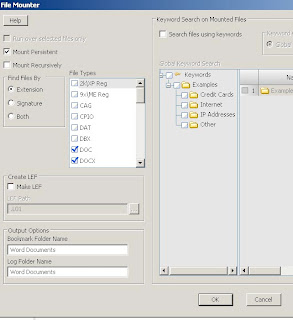
Figure 2 - Mounting Office Documents with File Mounter EnScript.
Once all the Office documents have been mounted you can extract all the OLE objects that are non-picture files with my OLExtract EnScript. Get it below.
OLExtract
This EnScript looks for all the OLENative Entries in the mounted documents and then extracts them to your EnCase default export folder. The EnScript will separate each file extracted in relation to which document it was extracted from and files with the same name will be incremented. The results of the execution of OLExtract will look similar to Figure 3 below.
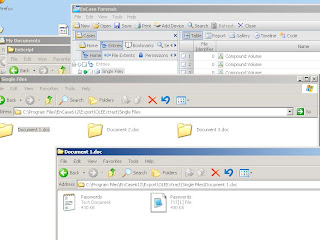
Figure 3 - Results of OLExtract
OLExtract will ignore jpegs stored as OLE objects because they are stored differently then other types of files stored in the document. You can extract jpegs easily from Office documents using file carving.

Figure 1 - Viewing Office Document "File Structure".
This also becomes a manual process viewing each document and then seeing what OLE objects are located in the document. EnCase recently came out with a way to automate the "View File Structure" process. The automated process is done with the File Mounter EnScript. This EnScript allows you to view the embedded file structure of many files such as Thumbs.db, zip archives, and Office documents (YES). Executing the process to automatically mount these types of files looks like Figure 2 below.

Figure 2 - Mounting Office Documents with File Mounter EnScript.
Once all the Office documents have been mounted you can extract all the OLE objects that are non-picture files with my OLExtract EnScript. Get it below.
OLExtract
This EnScript looks for all the OLENative Entries in the mounted documents and then extracts them to your EnCase default export folder. The EnScript will separate each file extracted in relation to which document it was extracted from and files with the same name will be incremented. The results of the execution of OLExtract will look similar to Figure 3 below.

Figure 3 - Results of OLExtract
OLExtract will ignore jpegs stored as OLE objects because they are stored differently then other types of files stored in the document. You can extract jpegs easily from Office documents using file carving.
Subscribe to:
Posts (Atom)